Imagination IS MORE IMPORTANT THAN KNOWLEDGE
Together we the people achieve more than any single person
could ever do alone.
GLINT
Success Is The Sum Of Small efforts
Together we the people achieve more than any single person
could ever do alone.
GLINT
FAILURE IS THE CONDIMENT THAT GIVES SUCCESS
With over 15 years of experience supporting various industries, including government agencies, educational and financial institutions, healthcare, and not-for-profit organizations, I am a knowledgeable cyber security professional driven to create proactive strategies that address daily operational challenges. I have had the opportunity to lead multiple projects aimed at deploying security solutions in response to critical client needs. My passion for this field has allowed me to consistently deliver results that exceed expectations. As a contractor, I have honed my skills in delivering holistic security solutions that cover various aspects of the client's operations. My ultimate goal is to ensure that clients can conduct their operations safely and securely, without losing sight of business objectives.
EXPERIENCE AND SKILL
A Cybersecurity Engineer with diverse technical abilities that enables a consistent record of delivering extraordinary results in technology deployments, optimization, operational performance, cybersecurity, and enterprise transformation, by supporting an organization’s core mission.
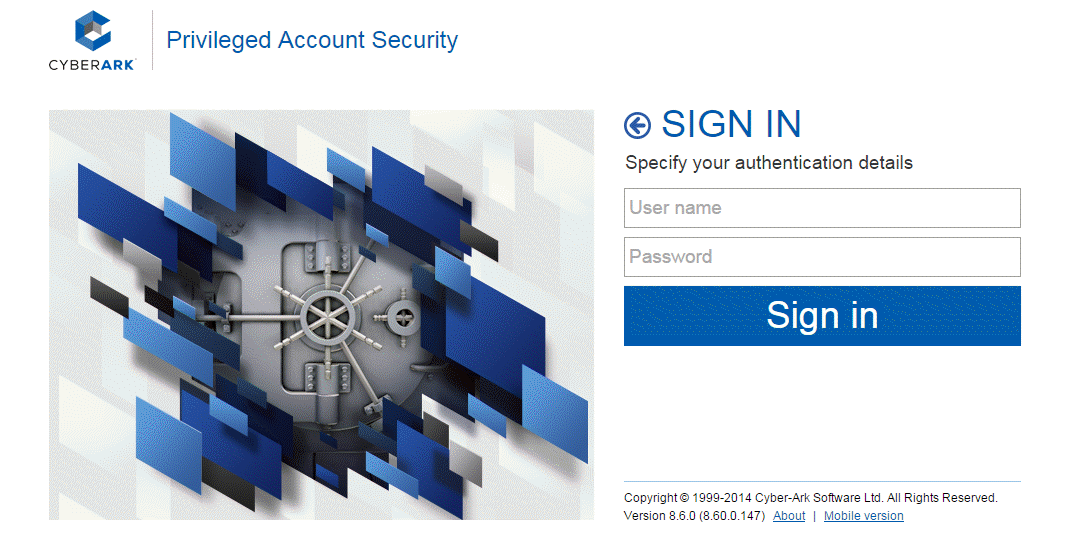
Security Delivery Manager
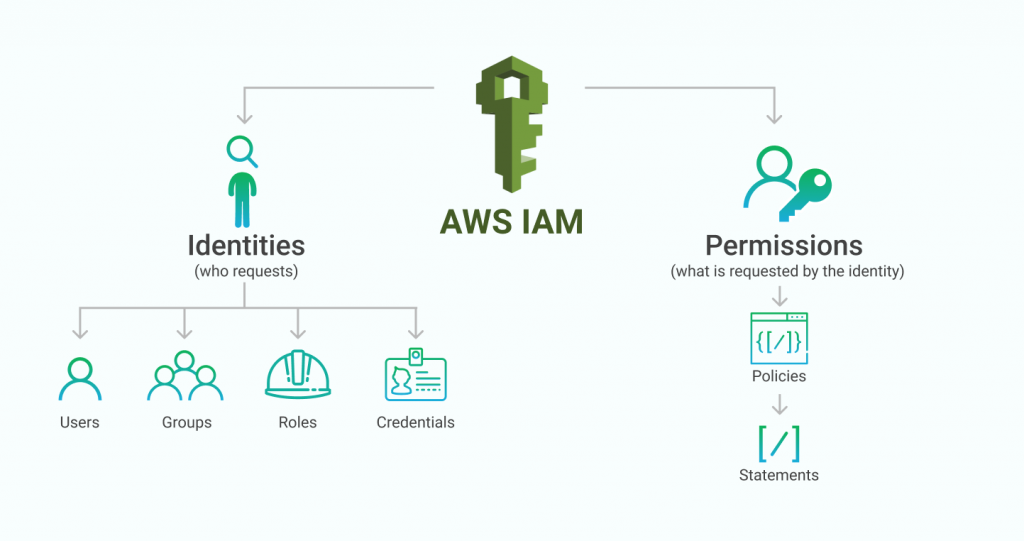
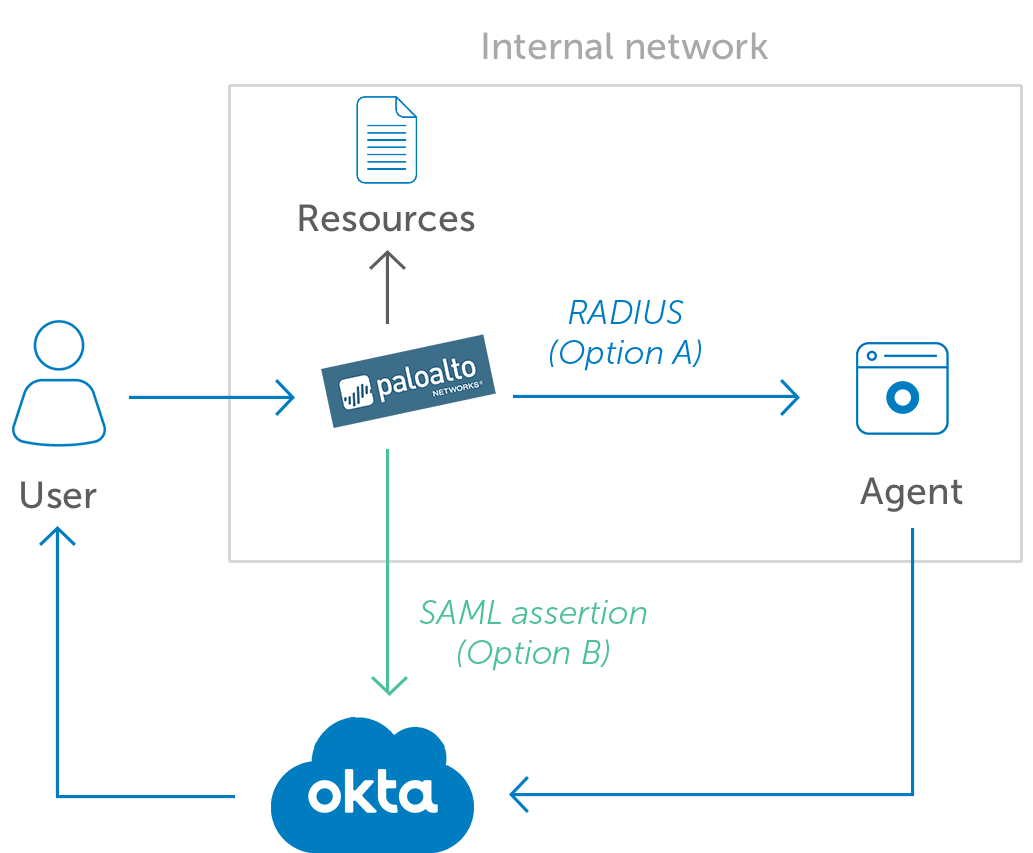
Currently working on multiple projects and programs assessing new technologies and builds supporting federal clients. Develop solution blueprints, design details, and lead change enablement. Lead team of Analysts and Engineers to redesign and improve an effective SOC solution for client. Advise clients on visibility tooling architecture, design principles, security best practices, engineering process and approvals. This includes research and identify gaps on various SOC processes that requires improvements, research and translate risk information on ICAM capabilities to support DOD 2027 ZTA mandates. Provide recommendations from identified capability gaps to increase cybersecurity, improve daily operations, and gain IT efficiencies. Support/capture business development opportunities related to transformation and cybersecurity, working directly with government leads, vendors, contractors, and team members to setup and integrate security tooling solutions, both on-prem and in the cloud. Deploy several security tools such as AWS, Azure, Tenable, CrowdStrike, Rapid7, dB protect, Vormetric, McAfee Mvision, Netskope, Splunk, Okta, Jira, Confluence, ServiceNow, Terraform, Postman, Salesforce, CyberArk, etc.
Security Engineer
Responsible for administering IT security controls to protect the confidentiality, integrity, and availability (CIA) of all corporate data. A central function of this role is to assist with the implementation of the strategic Information Security Plan. Utilized, configured, implemented, and maintained industry standard cyber defense capabilities including but not limited to web content filters, email security capabilities, advanced log analysis, network monitoring, network flow analysis, packet capture analysis, firewalls, anti-virus capabilities, vulnerability management, and access control lists (ACL). Implemented and integrated several security tools such as Microsoft cloud application security broker, tenable.sc, tenable.io, iboss, carbon black, rapid7, varonis, PhishMe, Qualys, Mcafee mvision (previously skyhigh security).
Security Coordinator
Responsible for the entire UHC IT infrastructure and security; this includes development of infrastructure design, architectures, and roadmaps in alignment with business needs and UHC IT strategy. A central function of this role is to target harmonization and standardization by implementing solutions. Planned, led, and coordinated the implementation of such solutions in close alignment with the various university wide IT departments and our external partners. Also accountable for the governance of the solutions and ensure that they maintain their integrity and remain standard solutions; this includes the overall operation of UHC infrastructure with respect to the fulfillment of service levels and that the operational environment meets university standards for security, performance, and regulatory compliance. Played a vital role in the migration of manual health records to electronic health record keeping. Involved in the implementation, deployment, and management of the EHR system, which includes a network consisting of windows, Mac osx, and linux operating systems, applications, file servers, firewalls, vpn, security policies, risk assessment, disaster recovery and business continuity.
LASTET WORKING PROJECT
Coming soon...
Colleagues SAYS
Coming soon...

Coming soon...
Abbas

Coming soon
Mohamed Alieu Jalloh

Coming soon...
Ryan Beckles
LATEST NEWS & BLOGS
Coming soon...
Stay up to date, subscribe to the free newsletter !
Like all networking protocols, UDP is a standardized method for transferring data between two computers in a network. Compared to other protocols, UDP accomplishes this process in a simple fashion: it sends packets (units of data transmission) directly to a target computer, without establishing a connection first, indicating the order of said packets, or checking whether they arrived as intended. (UDP packets are referred to as ‘datagrams’.)